How to generate API keys for users
API keys allow users and applications to authenticate programmatically with the Zeta Alpha platform without using passwords. This guide will walk you through the steps to create users and generate API keys for them.
Prerequisites
- Admin access to the Zeta Alpha Navigator
Overview
API keys can be generated for any user in your tenant. Users are created differently depending on your authentication method:
- Password authentication: Users must be manually created through the Navigator UI (see Step 1)
- SSO authentication: Users are automatically created when they first log in through your identity provider
Once a user exists in the system, you can generate API keys for them (Step 2).
Step 1: Ensure the user exists
For Password Authentication
If the user doesn't already exist, create them:
- Log in to the Zeta Alpha Navigator with admin credentials and click on the
Usersbutton under theManagementsection on the sidebar.
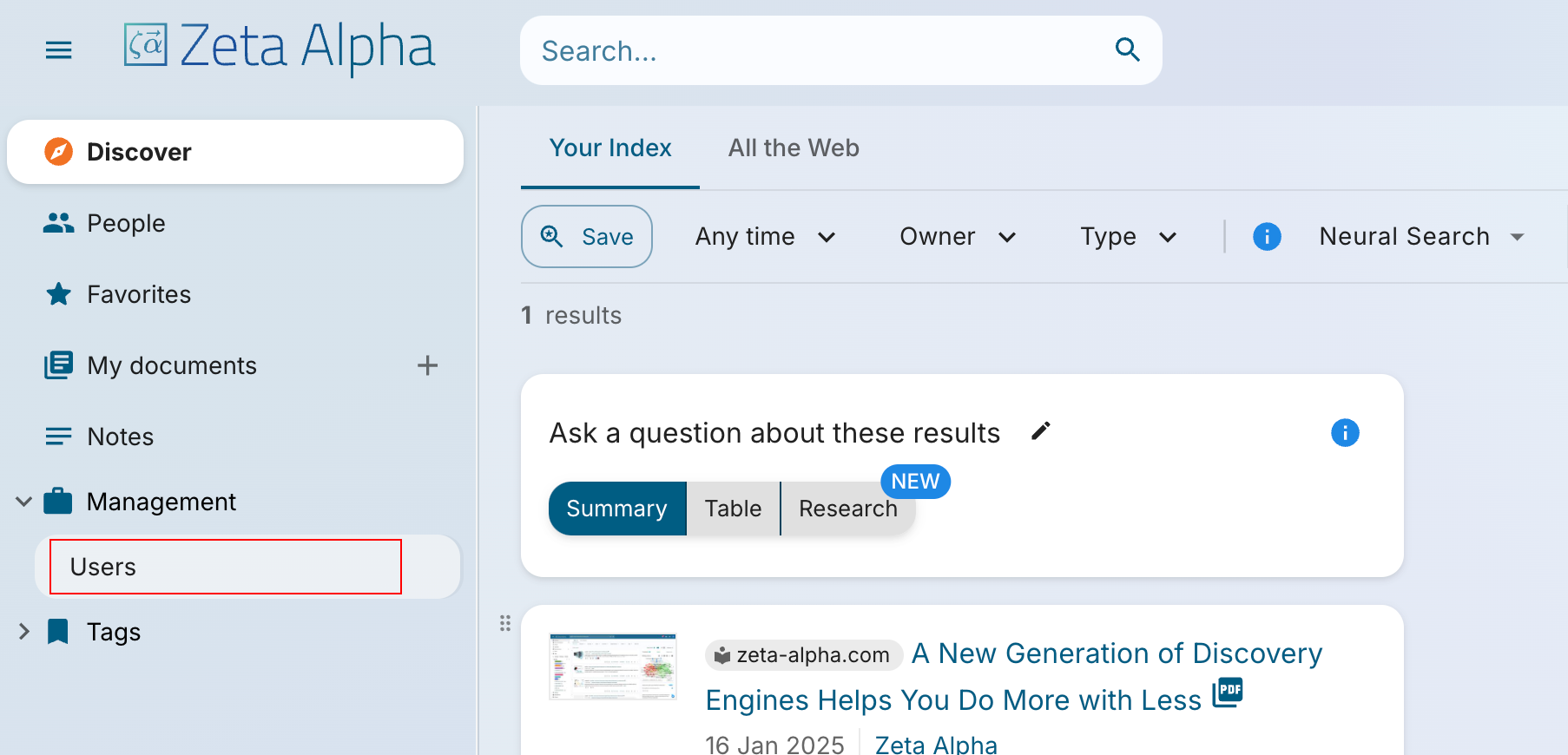
- On the Users page, click on the
New userbutton.
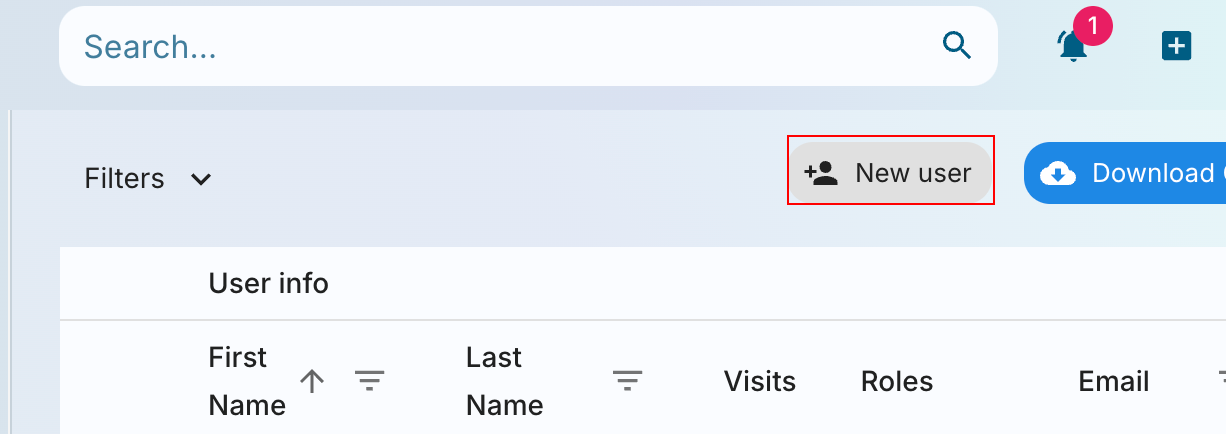
- Fill in the user details and click on the
Submitbutton.

For SSO Authentication
Users are automatically created when they first log in through your identity provider. Simply have the user log in once, then proceed to Step 2 to generate their API key.
Step 2: Generate an API key
Locate the user in the Users list and click on the pencil button to edit the user.
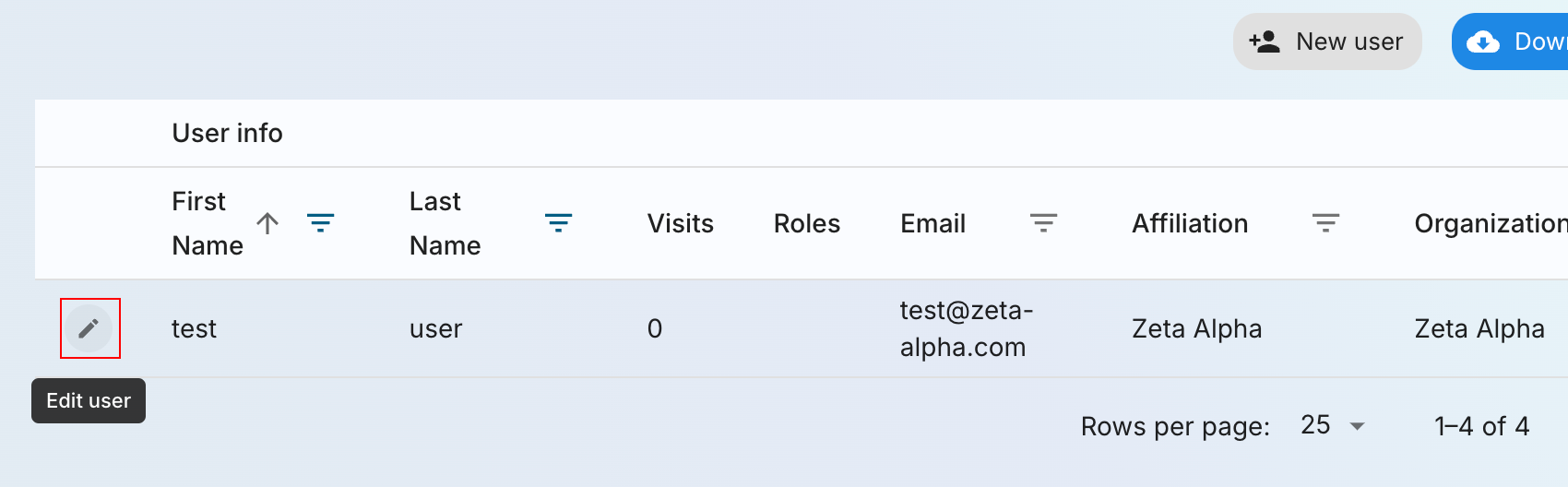
This will open a modal with the user details. Click on the API keys tab and then click on the + Add button.
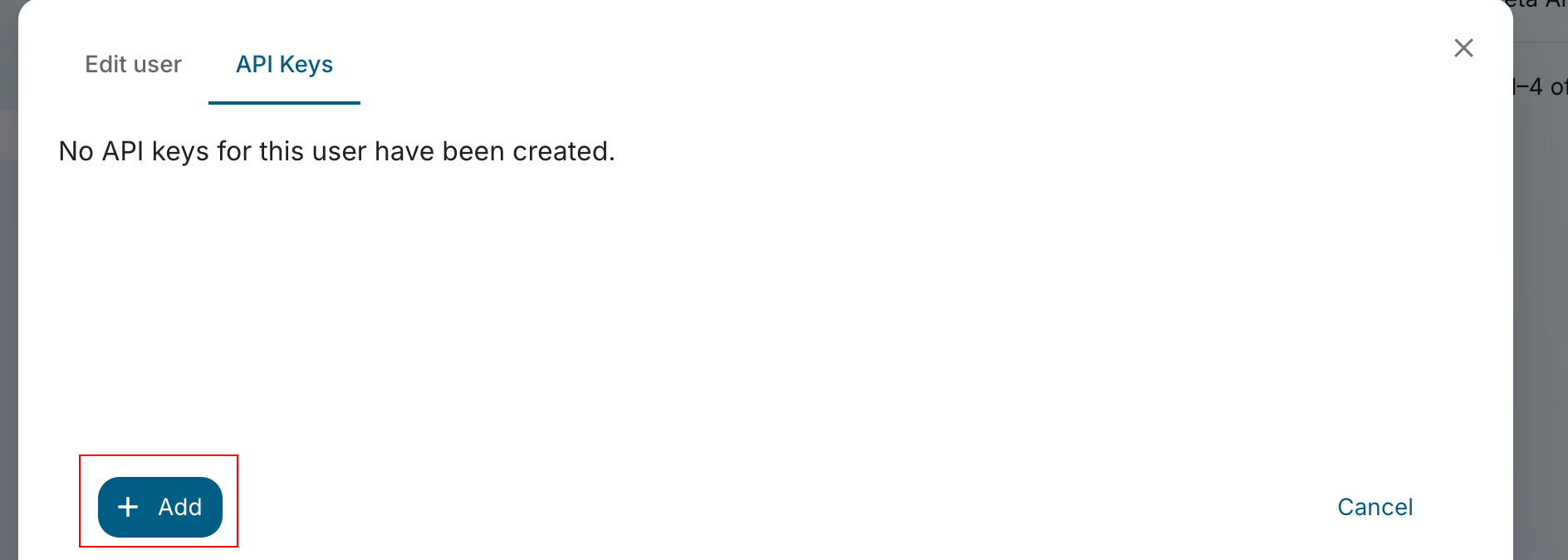
An API key will be generated for the user. Copy the API key immediately and save it in a secure location - you won't be able to view it again after closing this dialog.
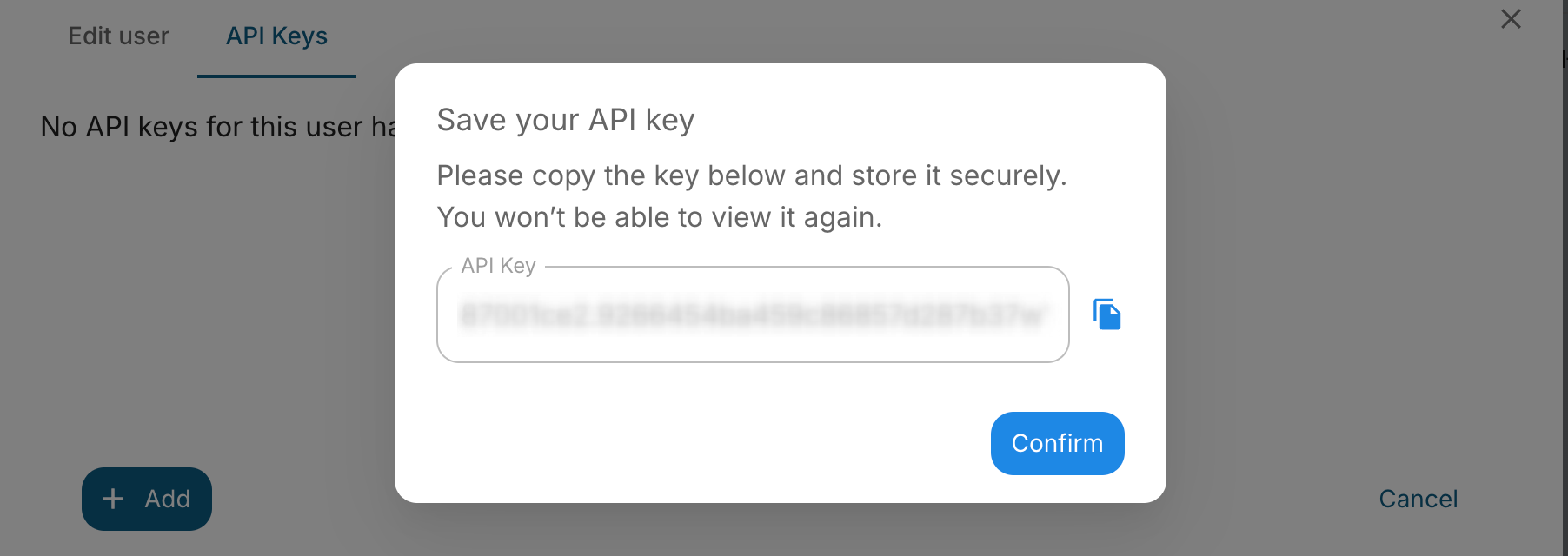
Using API keys
API keys can be used to authenticate API requests to the Zeta Alpha platform. Include the API key in the X-Auth header of your requests:
curl -H "X-Auth: YOUR_API_KEY" https://<your-tenant-url>/...
Managing API keys
Viewing existing keys
In the user edit modal under the API keys tab, you can see a list of all API keys associated with the user. The keys are masked for security, but you can see when each key was created.
Revoking API keys
If an API key is compromised or no longer needed, you can revoke it by clicking the delete button next to the key in the API keys list. Revoked keys cannot be restored.
Best practices
- Keep API keys secure: Treat API keys like passwords. Never commit them to version control or expose them in client-side code.
- Use separate keys for different applications: Create multiple API keys if you have different applications or environments, making it easier to revoke access to a specific integration without affecting others.
- Rotate keys regularly: Periodically generate new API keys and revoke old ones as part of your security practices.
Next Steps
- Change to use SSO Authentication - Configure single sign-on for your tenant.
- Create custom Indexes - Set up custom indexes for your data.
- Ingest documents with the Ingestion API - Start ingesting documents programmatically using your API key.